A Smarter Way to Audit Personnel Security
Why you should audit the employee lifecycle and pull in some IT controls as well.
Welcome to GRC Lab, a weekly newsletter where we provide actionable advice to help you launch, grow and accelerate your career in Governance, Risk and Compliance.
When you look at the ISO/IEC 27001 controls for personnel security, it’s easy to just go down the list. You start at the top and work your way to the bottom. Most auditors do exactly that.
It gets the job done, but it misses the bigger picture.
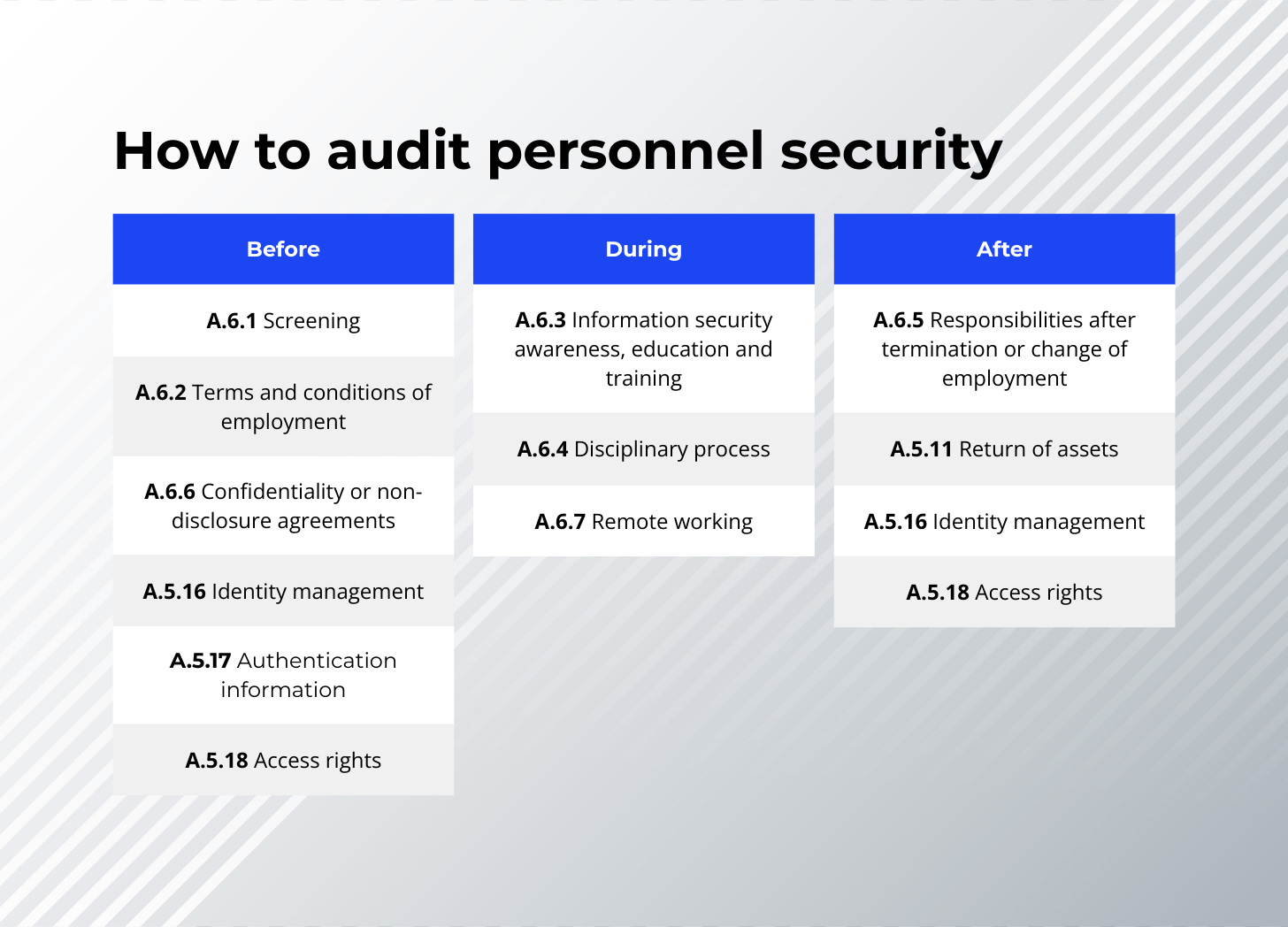
Here are the standard personnel security controls (A.6.1 – A.6.8) that you usually face:
A.6.1 Screening
A.6.2 Terms and conditions of employment
A.6.3 Information security awareness, education and training
A.6.4 Disciplinary process
A.6.5 Responsibilities after termination or change of employment
A.6.6 Confidentiality or non-disclosure agreements
A.6.7 Remote working
A.6.8 Information security event reporting
Auditing these in numerical order is fine, but it feels disjointed. Real life doesn’t happen in numerical order. A better approach is to audit the employee lifecycle.
By grouping these controls into “Before,” “During,” and “After,” you follow the actual path of a staff member. It also makes sense to pull in a few controls from outside the A.6 category. HR and IT have to talk to each other for security to work, so your audit should check those connection points too.
Here is how you could structure such an audit.
Phase 1: Before Employment (The Onboarding)
This is where you check how a person gets into the company. You are looking for the handoff between HR signing the paperwork and IT flipping the switch on access.
Start with the HR basics. You need to verify A.6.1 Screening to ensure background checks happen before the person starts. Then check A.6.2 Terms and conditions and A.6.6 Confidentiality agreements. These are your legal safety nets.
But paperwork doesn’t give a user access to the network. This is where you should bring in the “A.5” controls to see if the process actually works.
Ask how IT finds out a new person is starting (A.5.16 Identity management). If HR sends an email or opens a ticket, is it timely? Once IT knows the person exists, how do they know what folders or software to unlock? That’s A.5.18 Access rights. You want to ensure the new hire doesn’t just get “admin access” because it’s convenient.
Finally, check the logistics. How does the user get their initial password securely (A.5.17 Authentication information)? If they are sent a laptop or phone, track how those assets are assigned to them.
If you audit these together, you can catch the gaps where HR thinks IT is handling it, and IT thinks HR is handling it.
Phase 2: During Employment (The Working Life)
Once the employee is settled, the risks change. Now it’s about behavior.
Check A.6.3 Information security awareness. Are they actually learning anything, or just clicking “Next” on a slide deck? Look for evidence of real training.
You also need to look at A.6.7 Remote working. Since hybrid work is normal now, check the policy for working from home. Ensure the security rules apply just as strictly at a kitchen table as they do in the office.
And if someone breaks those rules? Check A.6.4 Disciplinary process. You want to see that there is a formal process for handling security violations, not just a verbal warning.
Phase 3: After Employment (The Offboarding)
This is usually the riskiest phase. When someone leaves, the clock starts ticking.
Start with A.6.5 Responsibilities after termination. HR should remind the departing employee that their confidentiality obligations don’t end just because their paycheck did.
Then, immediately pivot to the technical controls. This is often where the process fails.
Check A.5.16 Identity management and A.5.18 Access rights. How fast was the account disabled? Did it happen the minute they walked out the door, or a week later?
Don’t forget A.5.11 Return of assets. Verify that laptops, keys, and badges were collected and logged.
A Note on A.6.8
You might notice I left out A.6.8 Information security event reporting.
While it is technically a “people” control, it fits much better in an audit of Incident Management. Save it for that session. It makes more sense to discuss how people report bugs or breaches when you are already looking at how the company fixes them.
Cut Implementation Time in Half
If you want to learn how to implement ISO 27001 with this kind of practical logic, check out my ISO/IEC 27001 Lead Implementer course.
We don’t just read through the clauses. We look at how to build a security framework that actually fits a real business. You will learn how to interpret the requirements, connect the dots between different controls, and implement a system that passes audits without slowing down operations.