Ditch the PDFs: NIST's CPRT is Changing How GRC Pros Handle Cybersecurity Resources
Inside this Edition
Here’s what we got for you today:
Discover how the NIST Cybersecurity and Privacy Reference Tool is changing how GRC professionals interact with authoritative resources.
Don’t miss our latest YouTube video, “From Threats to Controls”.
Ever found yourself buried in a 200-page NIST PDF, Ctrl+F-ing your way through controls and guidelines, only to lose track halfway?
If that's your daily grind as a GRC practitioner, it's time for an upgrade. Enter NIST's Cybersecurity and Privacy Reference Tool (CPRT)—a game-changer that's making static documents feel like ancient history.
What is the CPRT?
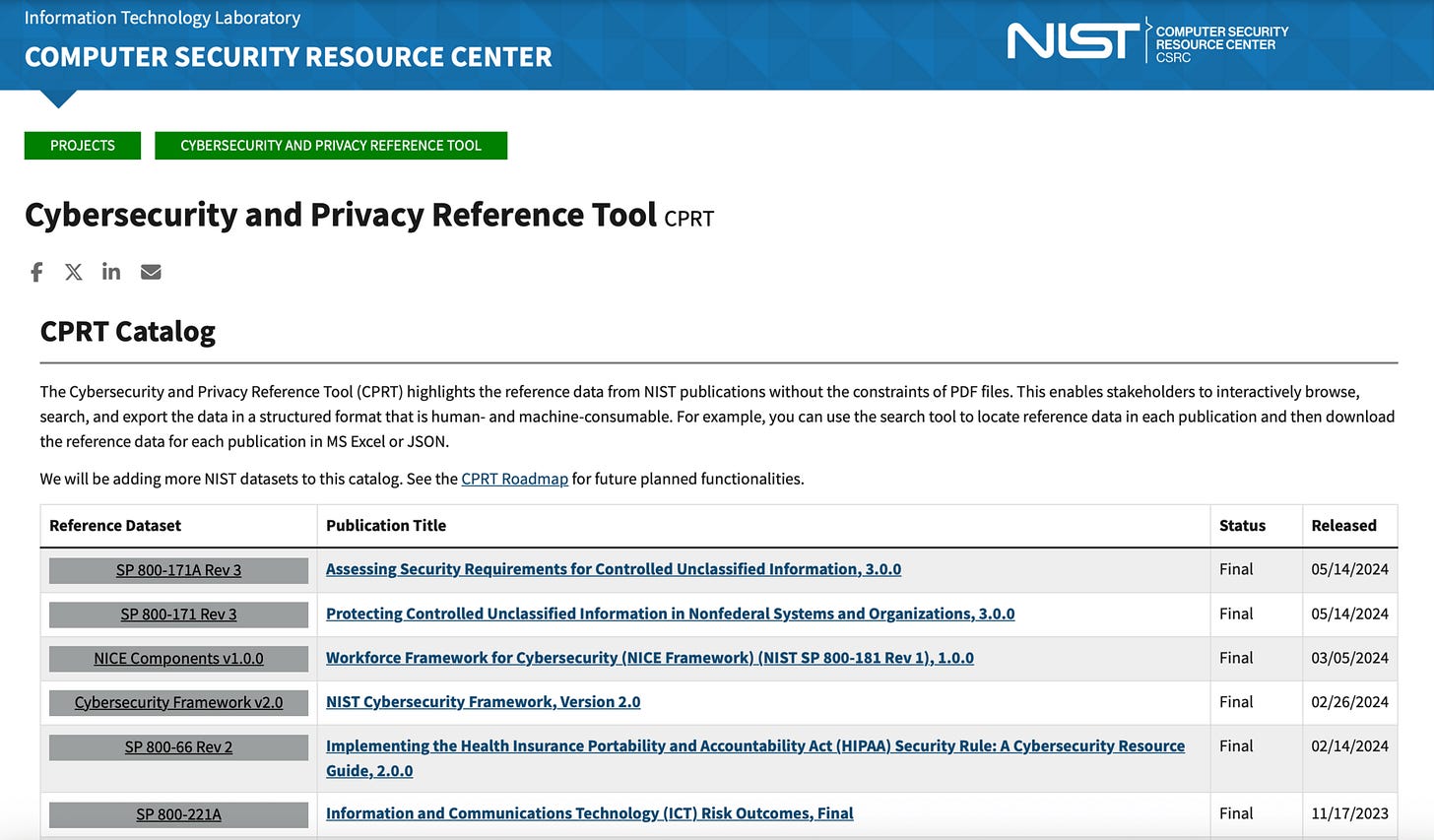
The CPRT, hosted by NIST's Computer Security Resource Center (CSRC), is an online platform that centralizes and digitizes key cybersecurity and privacy resources. Think of it as a smart library for NIST's flagship publications, like the Cybersecurity Framework (CSF) 2.0, SP 800-53 (Security and Privacy Controls), and SP 800-171 (Protecting Controlled Unclassified Information). Instead of downloading hefty PDFs, you get interactive access to reference data—controls, guidelines, and frameworks—in a structured, user-friendly format.
Launched to modernize how we interact with these resources, the CPRT turns complex docs into searchable, exportable datasets that make their content more accessible and easier to digest.
How CPRT Beats Traditional PDF Reading
Remember the frustration of cross-referencing multiple PDFs during a compliance audit? CPRT flips the script with features designed for real-world use:
Browsing Made Easy: Navigate through catalogs of publications like a digital bookshelf. Drill down into specific controls or sections without opening a single file.
Powerful Search: Use keywords to pinpoint exact references across documents. For example, search "data encryption" and get hits from CSF, SP 800-53, and more—in seconds.
Compare and Export: Side-by-side comparisons of controls from different frameworks? Check. Export data in machine-readable formats like CSV or JSON for integration into your GRC tools.
Real-World Wins for GRC Practitioners
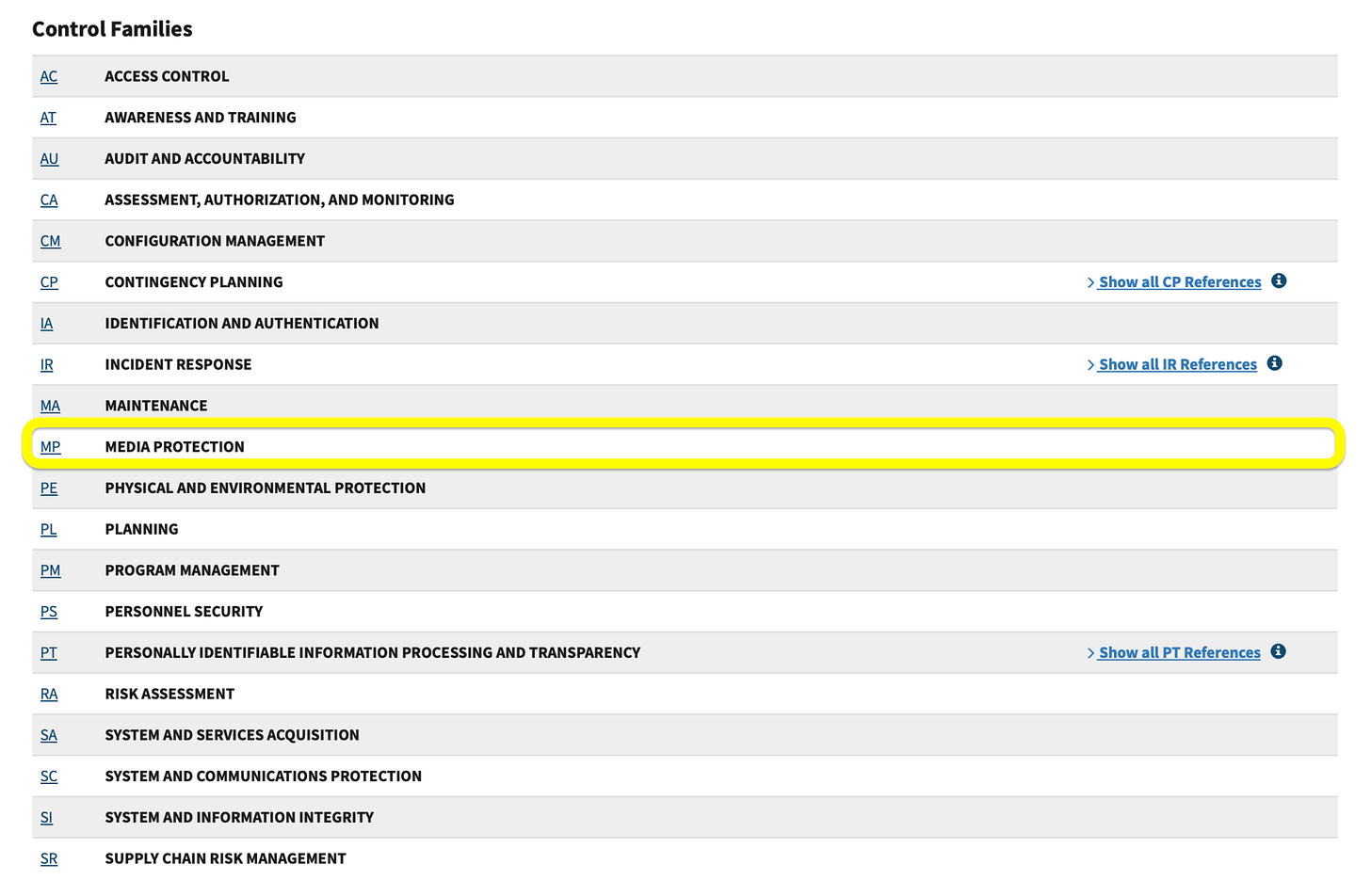
Imagine ensuring your organization complies with NIST SP 800-53's Media Protection controls for a system handling sensitive data. Traditionally, you'd juggle three PDFs: SP 800-53 for the control details, SP 800-53B for the control baselines (Low, Moderate, High), and SP 800-53A for assessment procedures. Tedious and error-prone.
With CPRT, it's really a breeze:
Navigate to the SP 800-53 catalog and select the "Media Protection" (MP) family from the 20 control families.
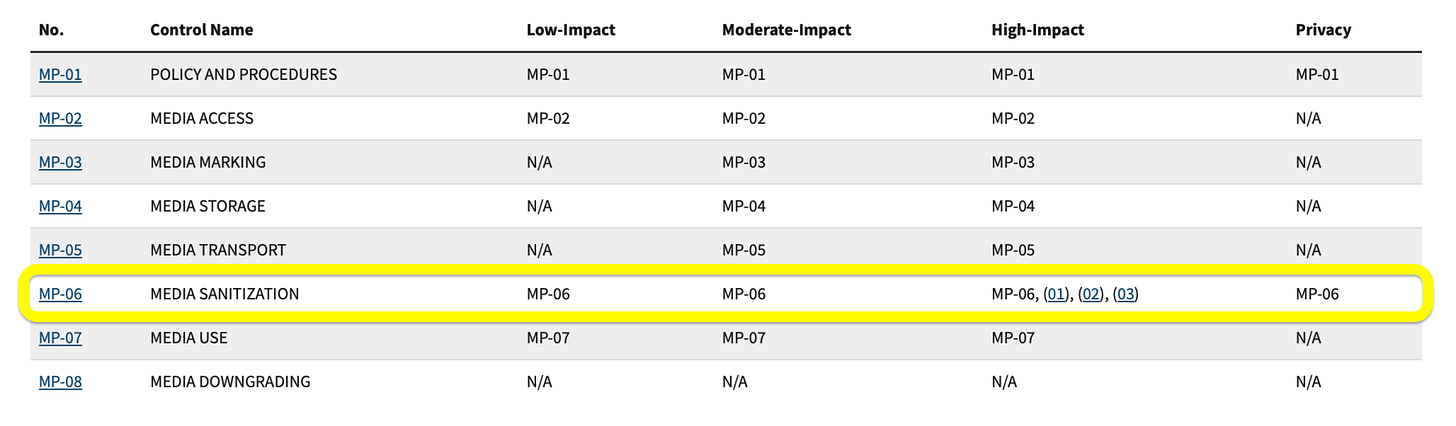
Click on MP-06 (Media Sanitization) to view its full details in one place.
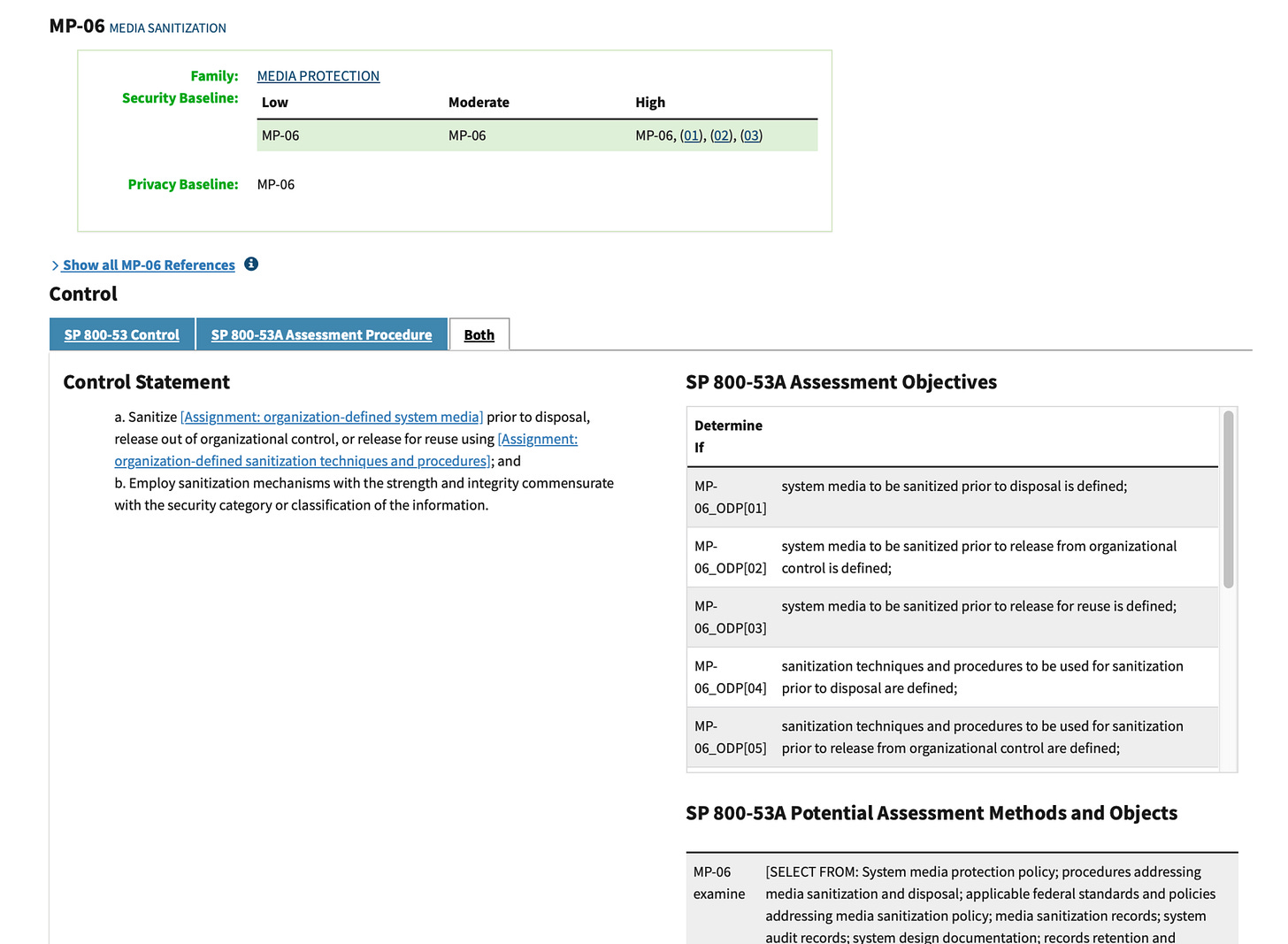
See the control's requirements (from SP 800-53), its baseline assignments (from SP 800-53B, e.g., included in Moderate and High baselines), and assessment procedures (from SP 800-53A) seamlessly combined.
This unified view saves hours of cross-referencing. For example, MP-06 requires sanitizing media before disposal or reuse, and CPRT shows you the exact methods (e.g., clear, purge, destroy), baseline applicability, and how to assess compliance—all in one interface. Early adopters report cutting research time by half, letting them focus on high-impact areas like emerging threats.
Ready to level up your GRC game? Check out the CPRT and explore a new way of working with their resources.
Cybersecurity and Privacy Reference Tool | CSRC
Our latest Video on YouTube
Have you ever wondered how threats, vulnerabilities and controls are related? If so, then our latest YouTube might have the answers to your questions. ↓
Test your Knowledge
Today’s question is from the CISM curriculum:
Which of the following metrics is MOST useful in evaluating the effectiveness of a security awareness program?
A) Number of training sessions conducted.
B) Employee feedback on training content.
C) Reduction in security incidents post-training.
D) Attendance rate for training sessions.
👉 Think you know the answer? Scroll down for the solution!
Answer: The correct answer is C.
A) The number of sessions does not indicate effectiveness.
B) Feedback is useful but not a direct measure of effectiveness.
C) A reduction in security incidents directly indicates the program's effectiveness.
D) Attendance rate shows interest but not effectiveness.