How to Solve the GRC Puzzle: A Roadmap Through the Noise
Welcome to GRC Lab, a weekly newsletter where we provide actionable advice to help you launch, grow and accelerate your career in Governance, Risk and Compliance.
I remember sitting in security meetings at the very start of my career, feeling completely lost. Words like ‘threat’, ‘vulnerability’, and ‘risk’ were tossed around interchangeably, and it felt like a game where the rules kept changing. I was confused, and honestly, sometimes irritated because what one expert explained to me often contradicted what the next one said.
It didn’t happen overnight. It took years of working in GRC and reading countless resources for the fog to lift. Slowly, but surely, I started to see the underlying structure. I realized that risks and controls weren’t just random components, but gears in a machine. I began to map out the relationships: how a threat needs a vulnerability to cause harm, and how that harm only matters if it touches the assets an organization actually cares about. Once I understood these connections, the noise faded.
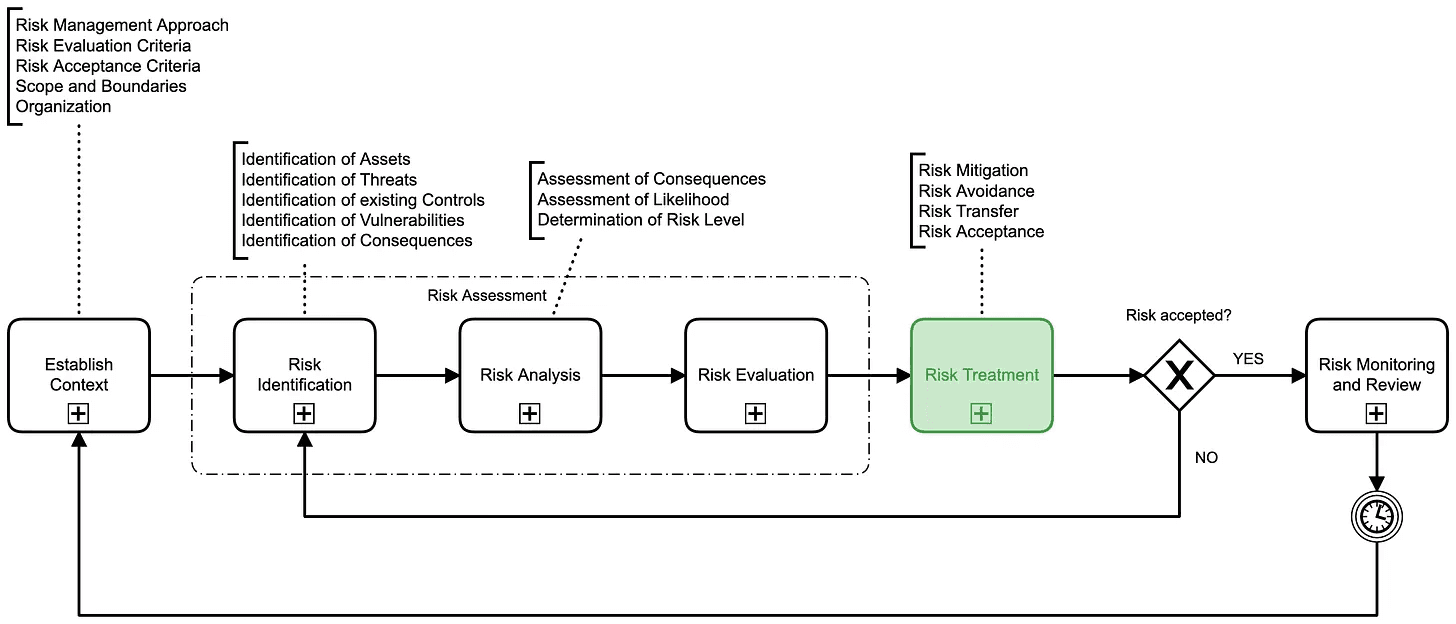
To understand how this machine works, we first need to look at the process that drives it: the Risk-Based Approach.
The Foundation: Risk Management
Information security management is about protecting organizations from potential events that can cause harm to their business. This is the risk-based approach.
Risk management is typically aligned with the following steps.
Establish Context
Before diving into risk identification or analysis, it’s crucial to establish the context in which the organization operates. This involves understanding the internal and external factors that can affect the organization’s assets. Establishing context provides a lens through which risks can be identified and evaluated.
Risk Identification
This stage involves identifying what could go wrong, how, and why. Similar to spotting the key players and strategies of an opposing team, risk identification is about recognizing the threat sources, threat events, vulnerabilities, and assets at risk. This provides a comprehensive list of risks that need to be further analyzed.
Risk Analysis
Once the risks are identified, they need to be analyzed to understand their nature, likelihood, and impact. Risk analysis provides a detailed view of each risk, helping the organization to prioritize them. This will help organisations to understand which scenarios are most likely to happen and how damaging they can be if not properly treated.
Risk Evaluation
Risk evaluation involves comparing the analyzed risks against pre-defined criteria to decide which risks need to be treated. This can be thought of as deciding which opponent’s plays need the most defensive focus. The evaluation helps in allocating resources more effectively by focusing on the most critical risks.
Risk Treatment
This stage involves selecting one or more options for modifying the risks and implementing those options. Risk treatment can involve risk avoidance, risk modification, risk sharing, or risk retention. Please note that the impact of risks can not be mitigated to zero. There will always be a residual risk, unless it can be completely avoided.
Risk Monitoring
Last but not least, risks need to be continuously monitored and reviewed to assess the effectiveness of the risk management process and to identify any changes in the risk landscape. I like to state that risks never retire. For the moment a risk might be properly taken care of, but as soon as a control fails, threats evolve, or new vulnerabilities arise, this risk must return to our attention.
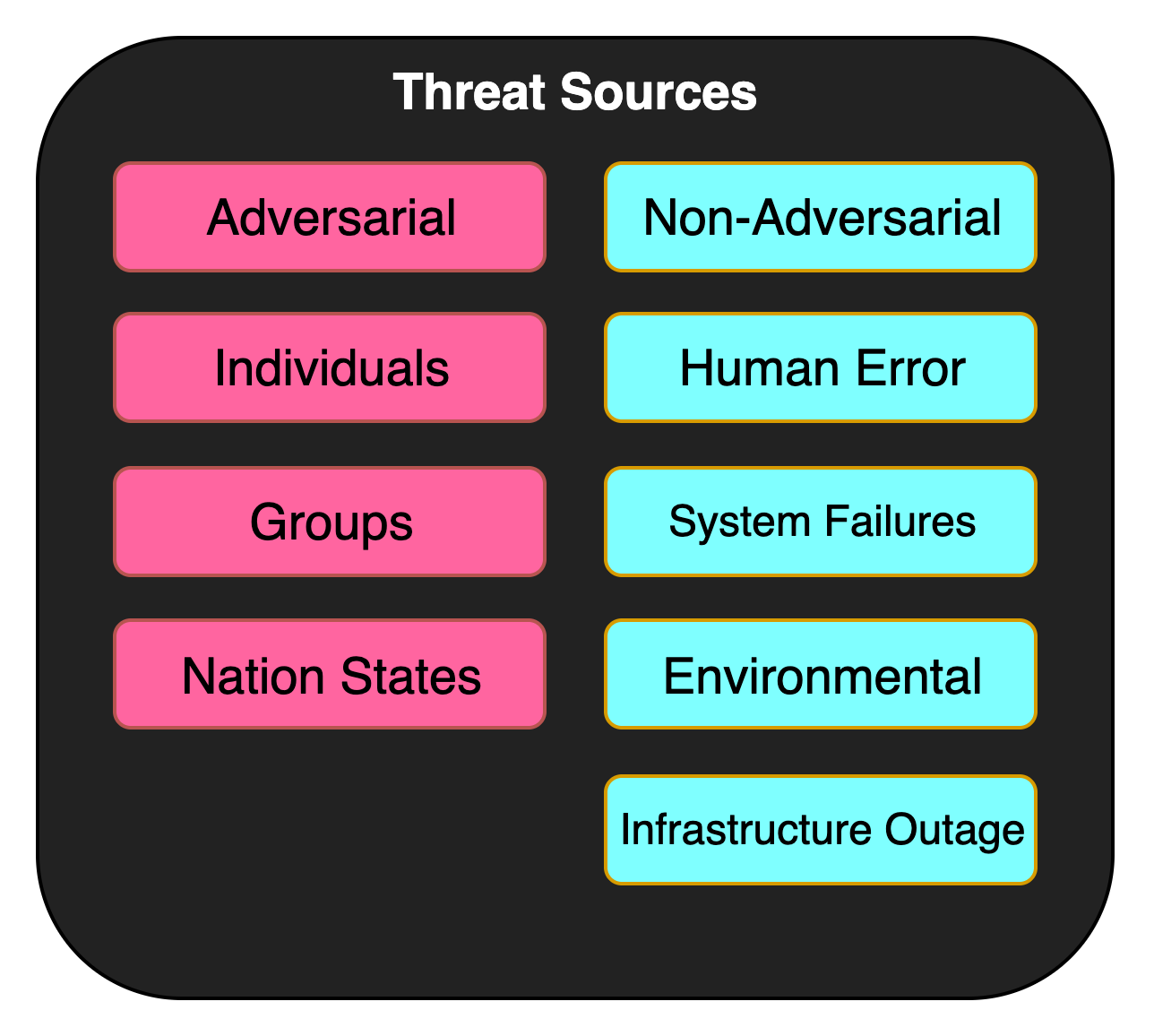
Threat Sources: The Starting Point
According to the National Institute of Standards and Technology (NIST), Threat Sources are defined as the origin of adverse events that could potentially harm an organization’s assets and operations. These sources can be intentional or unintentional and can come from a variety of places such as nature, individuals, or organizations.
NIST categorizes Threat Sources into two main types:
Adversarial: These are intentional actions taken by individuals, groups, or organizations with the motive of causing harm or exploiting vulnerabilities. Adversarial threats include hackers, terrorists, insider threats, and even competitors.
Non-Adversarial: These are unintentional actions or natural events that could potentially harm an organization but lack a targeted intent. Examples include natural disasters like floods or earthquakes, accidental data deletion by an employee, or system failures due to a bug.
By understanding the nature and types of Threat Sources as defined by NIST, organizations can better prepare for, and mitigate, various risks that may affect them.
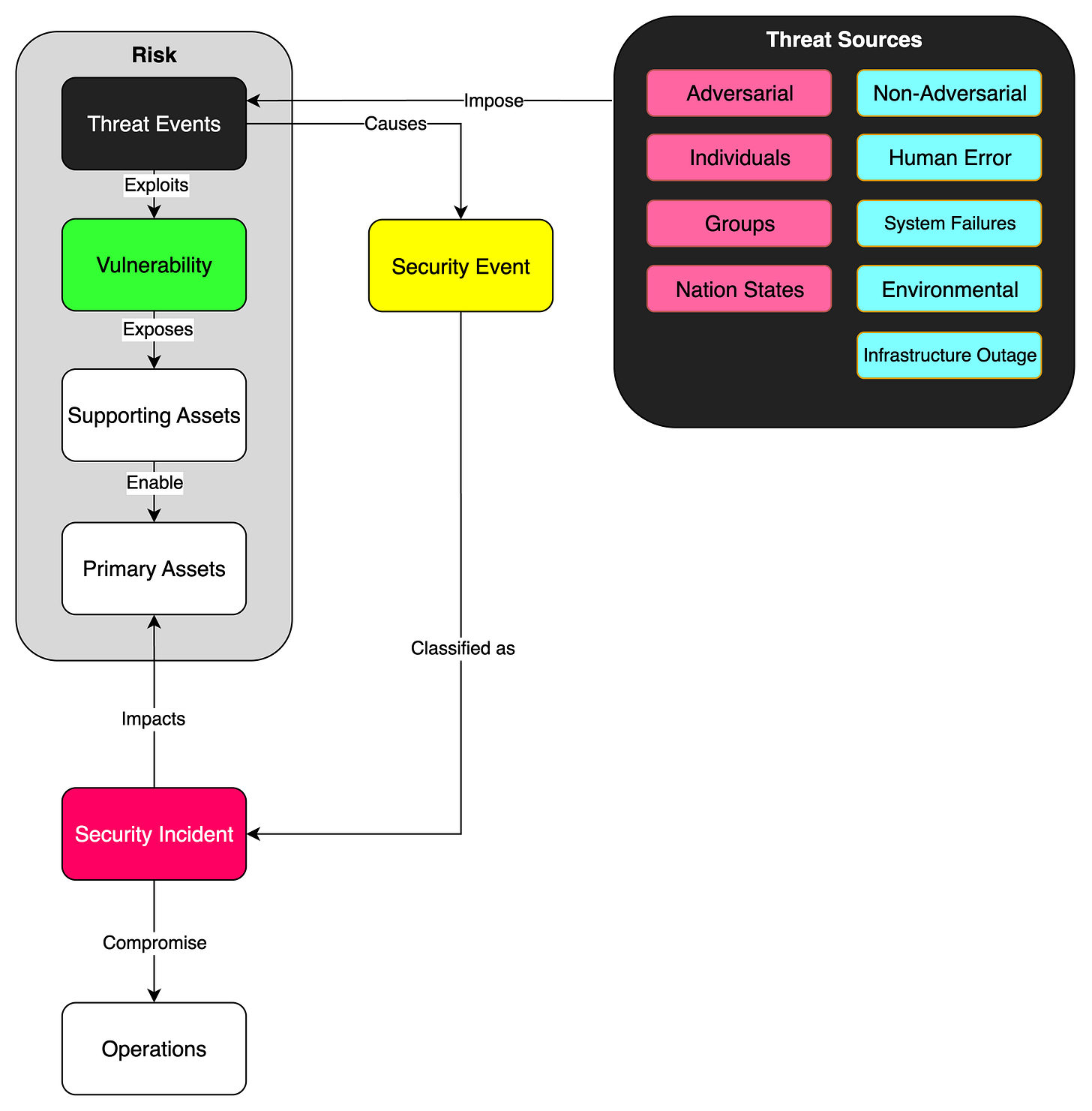
From Threat Sources to Threat Events
Threat Sources impose Threat Events, which are specific actions or incidents that can potentially harm your organization. For example, a hacker (Threat Source) might attempt to break into your network (Threat Event).
Vulnerabilities: The Weak Spots
Vulnerabilities are the weak spots in your system where Threat Events can sneak in. These could be outdated software, weak passwords, or even a staff member who’s not trained in security protocols.
Supporting Assets
Vulnerabilities often expose Supporting Assets, which are the various components of your system that aren’t core to your business but are still important. These can include:
Hardware: Servers, computers
Software: Applications, databases
Network: Internet connection, firewalls
Personnel: Employees, contractors
Sites: Physical locations like offices or data centers
Primary Assets
Primary Assets are what your business absolutely needs to function. These can be your main business processes or crucial pieces of information. Supporting Assets enable these Primary Assets to function. For example, your network (Supporting Asset) enables your online sales platform (Primary Asset).
The Chain Reaction: Security Events and Incidents
When a Threat Event exploits a vulnerability, it causes a Security Event. Not all Security Events are disastrous; some might be easily contained or harmless. However, when a Security Event has a significant negative impact, it is classified as a Security Incident. These incidents can compromise your operations and, ultimately, your Primary Assets.
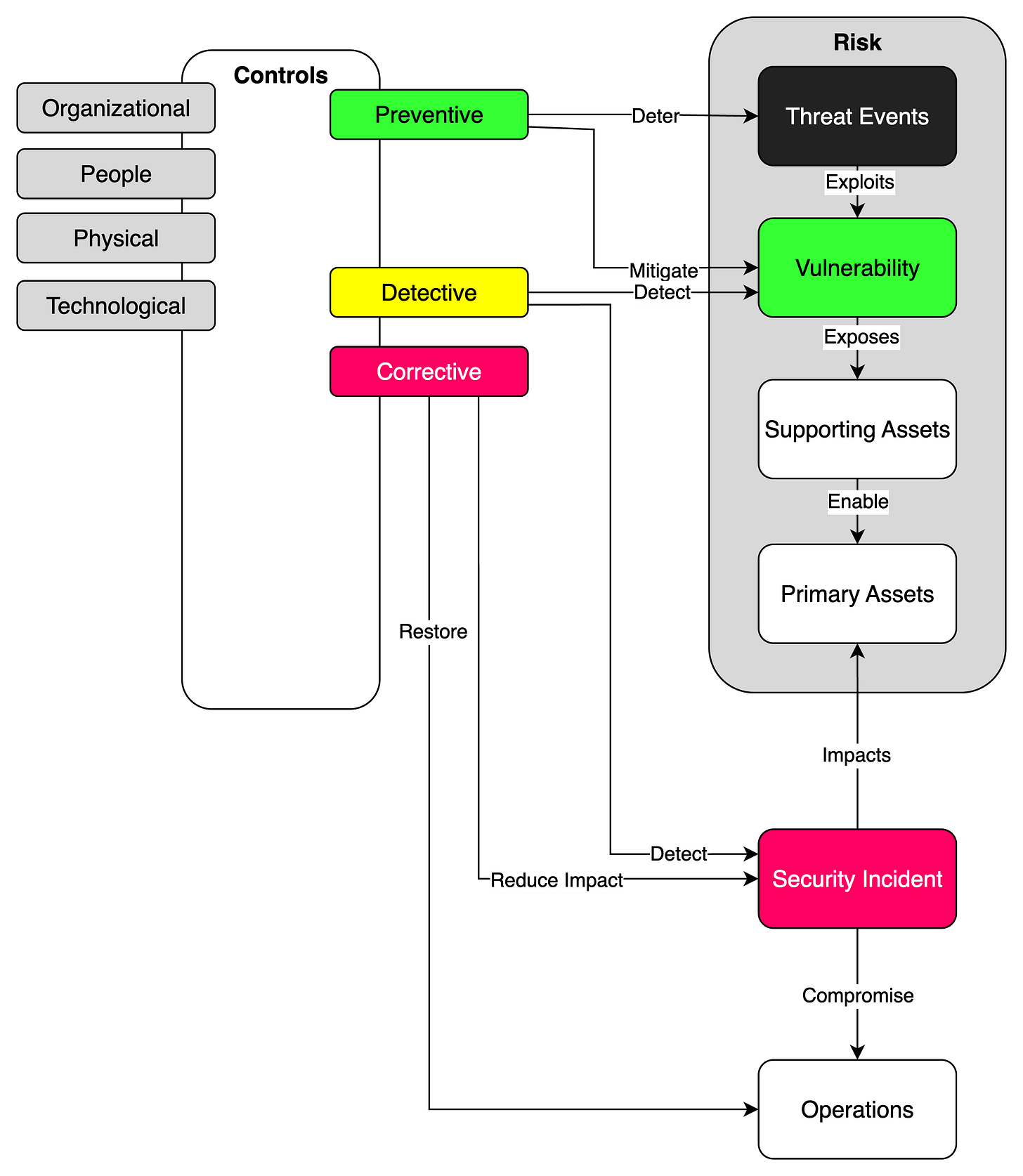
Implementing Controls Through Risk Treatment
Once you’ve identified your Threat Sources, analyzed your vulnerabilities, and assessed your risks, the next step is to implement controls to manage these risks effectively. In the realm of information security, controls are safeguards or countermeasures to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets.
Types of Controls Based on Risk Treatment
Controls are generally determined during the Risk Treatment phase and can be categorized into three main types:
Preventive Controls: These are measures designed to prevent an unwanted or unauthorized activity from occurring. They act as the first line of defense in risk mitigation. For instance, strong user authentication can prevent unauthorized access.
Detective Controls: These controls are aimed at detecting and alerting when an unauthorized or unwanted activity occurs. They don’t prevent an action but can trigger an alert or initiate corrective measures. An example would be intrusion detection systems that notify administrators about suspicious activities.
Corrective Controls: These come into play after a threat event has occurred, aiming to minimize the impact and bring the system back to its secure state. Data backups and system recovery plans are examples of corrective controls.
Make yourself irreplaceable, even to AI.
Understanding the theory is one thing; building a system that works in the real world is another.
If you want to move beyond the basics and learn how to construct an Information Security Management System from the ground up, my ISO/IEC 27001 Lead Implementer course is the perfect next step. We go deep into the practical application of these concepts, turning the “what” into the “how.”
November Sale:
I am currently running a special sale for the month of November. This is the perfect time to invest in your career and build skills that make you irreplaceable, even to AI. Don’t miss the chance to grab the course at a discounted rate before the month ends.