It’s Just Paperwork, Right?
How to make sense of policies, standards, and procedures.
Welcome to GRC Lab, a weekly newsletter where we provide actionable advice to help you launch, grow and accelerate your career in Governance, Risk and Compliance.
You’ve just been put in charge of “cybersecurity documentation.” Your boss wants policies. The auditors are asking for procedures. The IT team is talking about standards.
Where do you even begin? It’s a confusing mess of terms that all sound the same.
Most people see this as bureaucratic paperwork, digital dust piling up in a shared drive. But it shouldn’t be that way. A well structured documentation is the single best way to influence how staff and the organization as a whole work towards their objectives.
The problem is that most people, even inside large companies, don’t know how to distinguish them and can’t use them to their fullest potential.
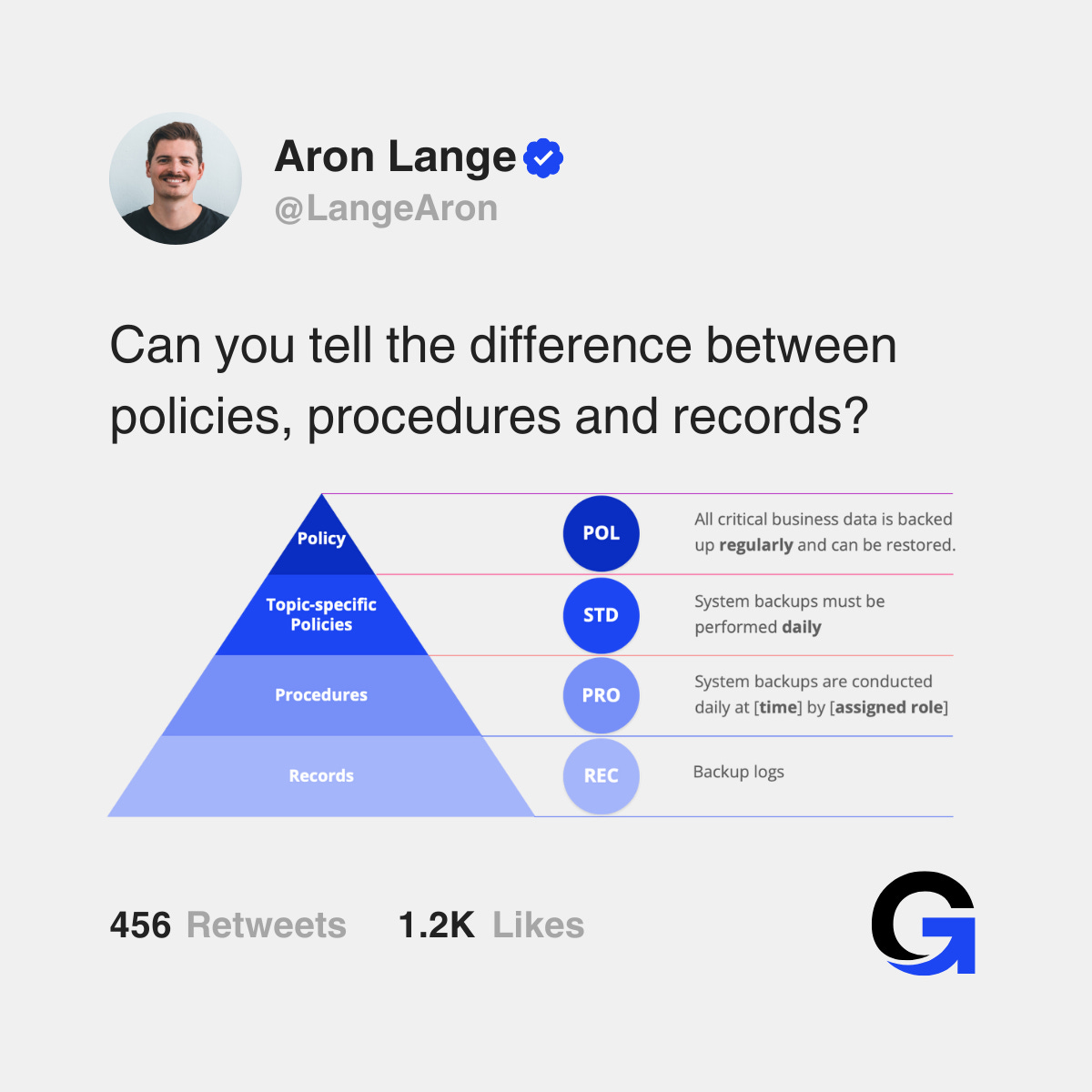
The policies, standards, and procedures in a cybersecurity documentation follow a top-down hierarchy. Each one answers a simple, specific question. This hierarchy is the backbone of major compliance frameworks, including the ISO/IEC 27000 series, or frameworks by NIST.
If you understand this structure, you can understand how any company really works—or build the structure yourself from scratch.
The structure is simple:
Policies answer: “Why?”
Standards answer: “What?”
Procedures answer: “How?”
Records prove the above
That’s it. That’s the entire system.
To make this clear, we’ll use one simple example from start to finish: data backup.
The “Why” — The Policy
A policy is the starting point. It is a high-level, mandatory statement from management. It answers the question, “Why are we even doing this?”.
A policy doesn’t give you technical details. It doesn’t name software or list server locations. Instead, it states a clear goal and grants the authority to get it done. In the language of compliance, it “establishes management’s intent”.
This is the document that a Chief Information Security Officer (CISO) uses to get a budget. It’s the “because the CEO and the board said so” document.
In the context of the ISO 27000 family, policies are the foundation of the entire Information Security Management System (ISMS). They are the top-level directives that all other rules flow from.
It’s worth noting that while this “Why, What, How” structure is a common hierarchy , different frameworks use different terms. The U.S. National Institute of Standards and Technology (NIST), for example, primarily focuses on ‘policies’ and ‘procedures’. In the NIST world, policies themselves are often tiered, broken down by their function, such as mission-level, business-process-level, and system-level policies.
Example: The Backup Policy
A backup policy is the perfect example. It won’t tell you how to back up data. It tells you why we back up data. A good one includes two main parts:
Purpose (The “Why”): It states the goal.
Real-world example: “The purpose of this policy is to maintain data integrity and availability... to prevent data loss... and to facilitate the restoration of... business processes”.
Or more simply: “Data backup is an integral part of disaster recovery planning”.
Scope (The “Who” and “What”): It defines who and what is covered.
Real-world example: “This Data Backup Policy applies to: IT infrastructure... Cloud or Third-Party hosted infrastructure... [and] Information Systems that process or store OU data”.
And: “This policy applies to all employees, contractors, and third-party employees... who... have access to the IT assets of the organization”.
That’s it. The policy is intentionally broad. It just set the goal: we must protect our data to keep the business running.
But it’s not actionable. You can’t “audit” a goal. You need a rule.
That brings us to the standard.
The “What” — The Standard
If the policy is the “why,” the standard is the “what.”
A standard is the “what” that we must do to meet the “why”. It translates the policy’s high-level goal into a mandatory, measurable, and quantifiable rule.
A quick note on terminology: In the ISO 27001 series, these measurable, granular rules are often referred to as “topic-specific policies”. For example, you might not have a “password standard” but a “topic-specific policy for access control”. Don’t let the name fool you. If it’s a mandatory, measurable rule that defines what to do (like encryption types or backup frequency), it’s acting as a standard.
This is the bridge from intent to action. It’s a “mandatory, specific requirement that defines what is needed to comply with a policy”.
A standard helps to enforce the statements of a policy.
Example: The Backup Standard
Our policy said, “we must protect our data”. The standard answers, “OK. What does ‘protect’ actually mean?”
The rules look like this:
The 3-2-1 Rule: This is the most famous data backup standard in the world. It’s a simple, clear, and measurable rule. As defined by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the 3-2-1 rule is :
3 – Keep three copies of any important file (one primary and two backups).
2 – Keep the files on two different media types (e.g., an internal hard drive and a cloud service).
1 – Store one copy off-site (outside your home or business).
Frequency: “Daily backups must be performed for all the components of critical systems”.
Retention: “System state backups must be retained for no less than 90 days and no more than one year”.
Testing: “Backup media must be tested periodically and at least once a year to ensure it meets... specifications... and functions as intended”.
Access: “Access... to backups, backup media... and restoration capabilities must be restricted and limited to authorized users only”.
See the difference? These are rules you can audit. An auditor doesn’t ask, “Do you believe in backups?” (the policy). They ask, “Show me your 90-day retention logs” and “Show me the test results from your last off-site restore” (the standard).
This is the document that forces a company to stop talking and start doing.
But it still doesn’t tell an employee how to do the test.
That brings us to the procedure.
The “How” — The Procedure
If the policy is the “why” and the standard is the “what,” the procedure is the “how.”
A procedure is the “how-to” guide. It is a detailed, step-by-step instruction manual that tells an employee exactly how to follow the standard.
The definition is beautifully simple. An official ISO glossary defines a procedure as: “A detailed description of the steps necessary to perform specific operations in conformance with applicable standards”.
This is the ground-level document. It’s the “recipe”. It’s the only document of the three that a non-managerial employee actually uses to do their job.
And in the event of a crisis, it is the most important document in the company.
Example: The Backup Procedure
Let’s follow the chain:
Policy (Why): “We must be able to restore business processes”.
Standard (What): “We must test our restores at least once a year”.
Procedure (How): “Here is the 9-step checklist for IT staff to perform the annual restore test.”
A real procedure for data restoration, based on university and IT documentation, looks like this :
IT Staff will determine the time and date of the lost data.
IT Staff will determine the appropriate backup media to restore the data.
IT Staff will insert the backup media into the appropriate server.
IT Staff will invoke the Backup/Restore software (e.g., Veritas Backup Exec or Arcserve).
IT Staff schedule the restore of the appropriate data within the Backup/Restore software.
IT Staff monitor the restore of data.
Upon restore, IT Staff evaluate the integrity of the restored data.
IT Staff will contact the end-user of the data to finalize restore.
Upon approval from the end-user, the restore is considered finished.
This is not a high-level goal. It’s a checklist. It’s ground-level, actionable, and vital.
With procedures we make sure that the rules, defined in our standards are operationalised.
The “Proof” — The Records
If the procedure is the “how-to” guide, the record is the “proof of work.”
A record is the evidence that a policy was followed, a standard was met, and a procedure was executed. It’s the log file, the completed checklist, the signed form, or the audit trail that proves an action took place.
This is the single most important part of an audit. An auditor doesn’t just read your procedure; they ask for the records to prove you followed it. This documentation provides the “chronological trail of system activity” that compliance bodies need to see.
Let’s complete our backup chain:
Policy (Why): “We must be able to restore business processes”.
Standard (What): “We must test our restores at least once a year”.
Procedure (How): “Here is the 9-step checklist for IT staff to perform the annual restore test.”
Record (Proof): “Here is the completed, backup job, on our backup server.
All together, this is the evidence that creates accountability.
Why This Matters to You
This hierarchy isn’t just for auditors. It’s a diagnostic tool for anyone.
When you’re looking at a company (as an employee, an investor, or a customer), you can use this framework to see if they’re serious about security or just paying lip service.
Policy with no Standard? This is a “Culture of Intent.” Management has “all talk, no action.” They’ve stated a goal but have no measurable rules to make it happen.
Standard with no Procedure? This is a “Culture of Ticking Boxes.” The company has a rule, but they’ve never created a step-by-step guide for anyone to actually follow it. The rule exists for an audit, but it’s not part of the daily operation.
All three are aligned? That is a “Culture of Maturity.” It shows that a high-level goal (the “why”) has been successfully translated into a measurable rule (the “what”) and a ground-level checklist (the “how”).
So, the next time you hear about cybersecurity documentation, don’t think of it as “just paperwork.”
Think of it as a “Why, What, How” chain. It’s the blueprint of the company’s true priorities. And now you know how to read it.
Whenever you’re ready, there are 3 ways how we can help you:
ISO/IEC 27001 Lead Implementer Course: Learn how to implement, and maintain an ISMS. Leverage ready-to-use templates designed to accelerate your certification journey.
Exam Vouchers: Prepare and certify with confidence. Purchase exam vouchers and add official, exam-aligned training material. Save 10% compared to official retail prices.
Promote your business: Put your company in front of 7,000+ highly-engaged GRC professionals at a 51% open rate!