The Missing Link in your Documentation
Discover the difference between processes and procedures.
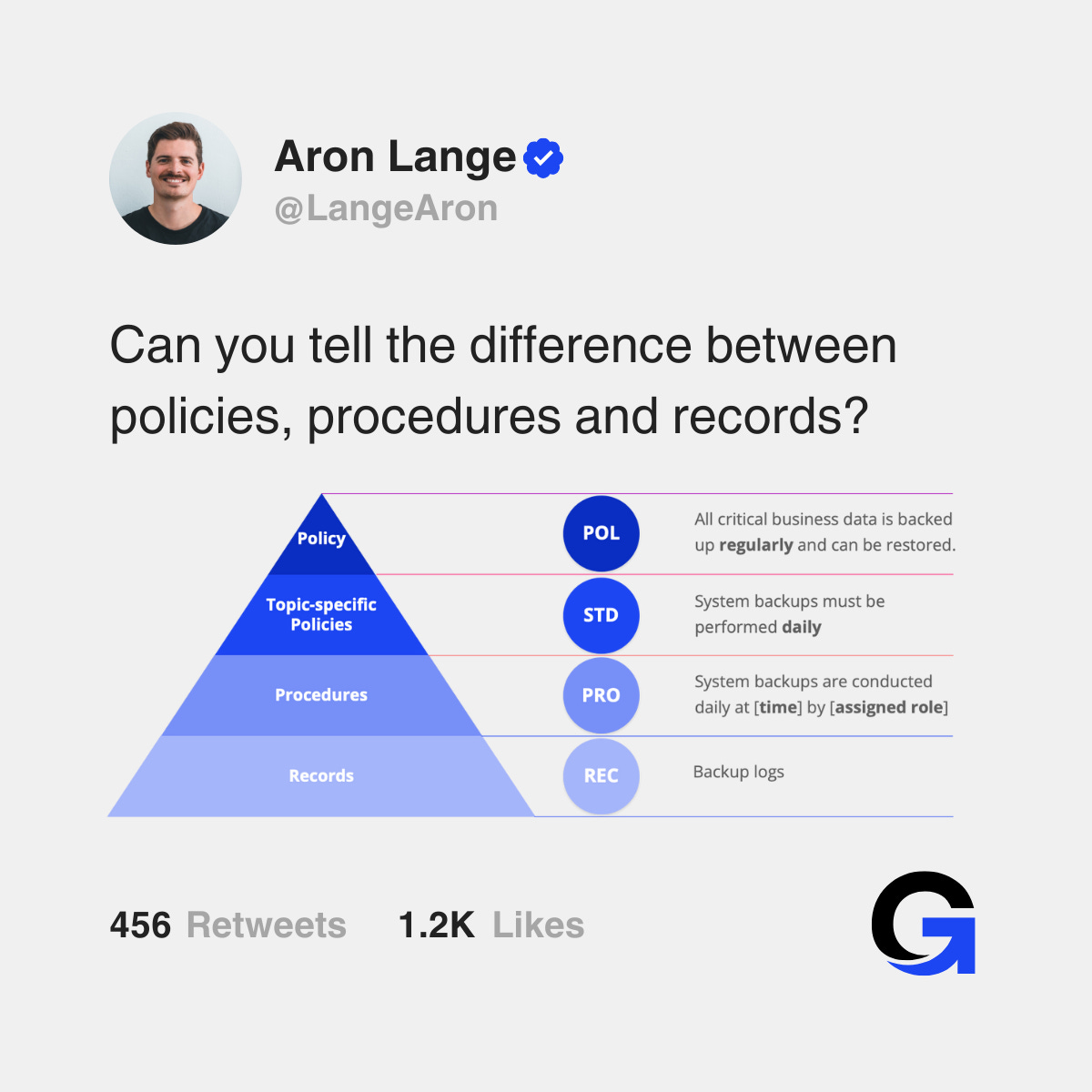
A solid information security program is built on a pyramid of documentation. At the top, you have high-level policies that state management’s intent. Below that are standards, which define mandatory rules. At the base, you have detailed, step-by-step procedures that tell employees exactly how to perform specific tasks. Records provide the evidence that procedures have been followed to meet standards that fulfil an organisation’s policies.
But there’s often a crucial layer missing from this formal documentation pyramid: the process. While procedures are a core component of the pyramid, processes are frequently left undocumented. This isn’t because they are unimportant; in fact, they are vital for understanding the big picture. The reason they are often omitted is that a process isn’t a document itself—it’s the action, the end-to-end flow of work that delivers a result.
Let’s break down why that is, starting with what a process truly represents.
What is a Process? The Strategic “What” and “Why”
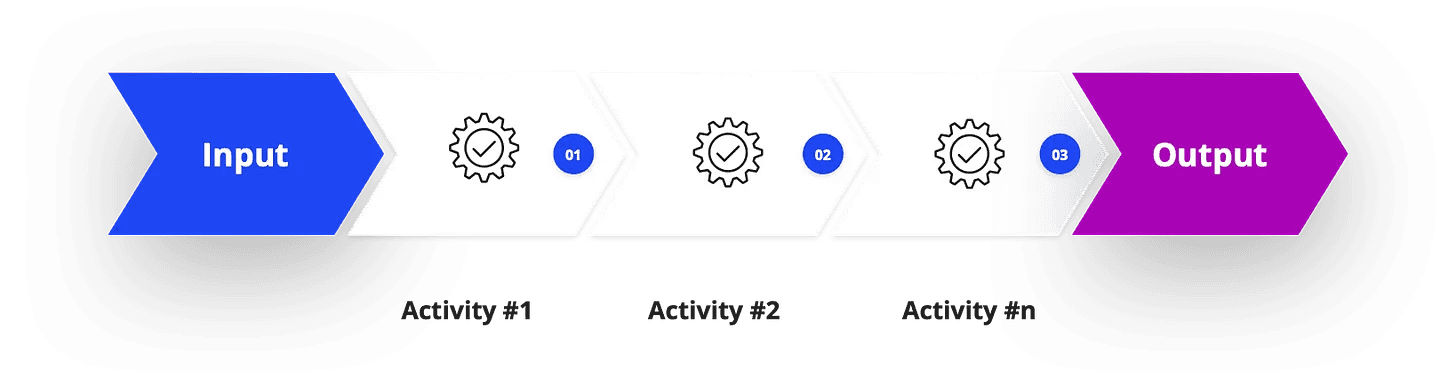
A process is a high-level series of related activities that transforms an input into a valuable output. It answers the questions, “What needs to be done?” and “Why are we doing it?”.
According to ISO 9000:2015, a process is defined as:
“A set of interrelated or interacting activities that uses or transforms inputs to deliver a result.”
A process provides the overall framework and direction but doesn’t get into the granular, step-by-step details. It’s the strategic roadmap, not the turn-by-turn directions.
Example: The Incident Management Process
A perfect example is the Incident Management Process. This is the entire lifecycle for handling a security event, from initial alert to final resolution. The goal (the “why”) is to minimize damage and restore normal operations as quickly as possible. The process (the “what”) is a sequence of high-level activities. According to frameworks from SANS, ISO and NIST, these activities typically include :
Preparation: Getting ready before an incident occurs.
Identification (or Detection & Analysis): Recognizing that an incident has happened and figuring out its scope.
Containment: Stopping the incident from spreading and causing more damage.
Eradication: Removing the threat from the environment.
Recovery: Restoring affected systems back to normal operation.
Lessons Learned (or Post-Incident Activity): Reviewing the incident to improve for the future.
This sequence describes the entire flow of work. It tells you what needs to happen, but it doesn’t tell you exactly how to perform each of these activities. For that, you need procedures.
What is a Procedure? The Tactical “How”
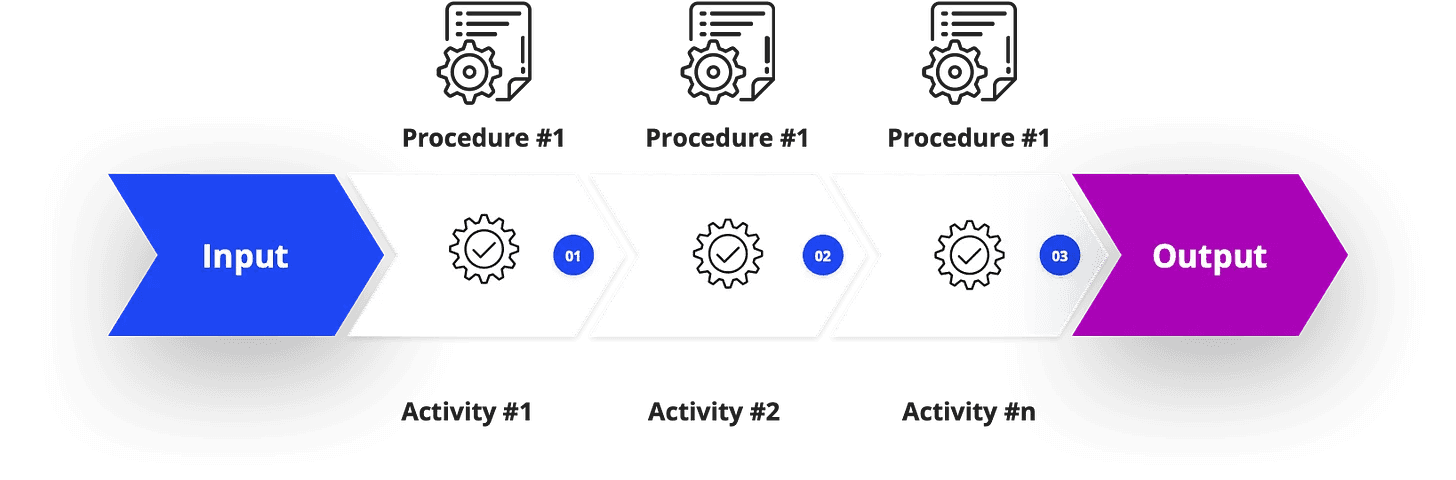
A procedure on the other hand is a detailed, step-by-step set of instructions that explains how to perform a specific activity within a process. It answers the questions, “Who does what, when, and how?”.
According to ISO 30000:2009, a procedure is defined as:
“A specified way to carry out an activity or a process.”
Unlike a process, which is flexible, a procedure is intentionally rigid and prescriptive to ensure tasks are performed with consistency and precision every time. You can’t have a procedure without an underlying process, but a process can exist without a documented procedure.
Example: Procedures within the Incident Management Process
Let’s zoom in on our Incident Management Process and see the specific procedures that bring each activity to life.
Activity: Identification
Procedure: End-User Reporting a Phishing Email. This document would give an employee exact, step-by-step instructions:
Do not click any links or open any attachments in the suspicious email.
If you are using Microsoft Outlook, click the “Report Phishing” button on the Home ribbon.
Alternatively, forward the email as an attachment to
abuse@yourcompany.com.If you accidentally clicked a link or entered your password, immediately call the IT Help Desk at extension 5555 and report it.
Activity: Containment
Procedure: Isolating a Compromised Host from the Network. This is a technical guide for a security analyst, detailing the precise actions to take once a machine is confirmed to be infected:
Open the Cortex XDR console and locate the compromised endpoint by its hostname.
Right-click the endpoint and select “Isolate Endpoint” from the action menu.
If the endpoint is a Linux server, log in to the firewall administration panel.
Create a new rule to block all inbound and outbound traffic for the server’s IP address, except for connections from the security team’s designated IP range.
Activity: Lessons Learned
Procedure: Conducting a Post-Incident Review. This procedure ensures that every incident review is thorough and consistent. It would instruct the Incident Commander to:
Schedule a post-incident review meeting within 48 hours of the incident’s resolution.
Complete the official “Post-Incident Review Template” document.
In the “Incident Timeline” section, document the key actions taken in chronological order.
In the “Root Cause Analysis” section, identify the primary cause and any contributing factors.
In the “Action Items” section, create a task list with assigned owners and due dates for all preventative measures identified.
As you can see, the process provides the high-level framework, while the procedures provide the detailed, actionable instructions needed to execute each part of that framework correctly and consistently.
Sample Lecture
Here is a sample lecture of our ISO/IEC 27001 Lead Implementer course on the fundamentals of documented information in the context of clause 7.5 of ISO/IEC 27001:2025.
Whenever you’re ready, there are 3 ways how we can help you:
ISO/IEC 27001 Lead Implementer Course: Learn how to implement, and maintain an ISMS. Leverage ready-to-use templates designed to accelerate your certification journey.
Exam Vouchers: Prepare and certify with confidence. Purchase exam vouchers and add official, exam-aligned training material. Save 10% compared to official retail prices.
Promote your business: Put your company in front of 7,000+ highly-engaged GRC professionals at a 51% open rate!