Why you shouldn't use Annex A
And Why NIST SP 800-53 Is The Ideal Companion
Inside this Edition
Here’s what we got for you today:
Learn why and how to combine NIST SP 800-53 with ISO/IEC 27001 to take your GRC program to the next level.
Be among the first to hear about our upcoming GRC bootcamps.
Why you shouldn’t use Annex A
Ever poured hours into mapping out security controls from ISO 27001's Annex A, only to realize they feel more like vague suggestions than actionable steps? You're not alone, this is a common pitfall that leaves many GRC teams scratching their heads.
But what if I told you Annex A isn't meant to be your control catalogue at all? Let's unpack this misconception and explore why NIST SP 800-53 might be the upgrade your compliance program needs.
The Role of Annex A in ISO 27001
Annex A in ISO 27001 is frequently misunderstood as a complete control catalog. In reality, it’s more of a checklist to ensure that no important controls have been overlocked or ommitted.
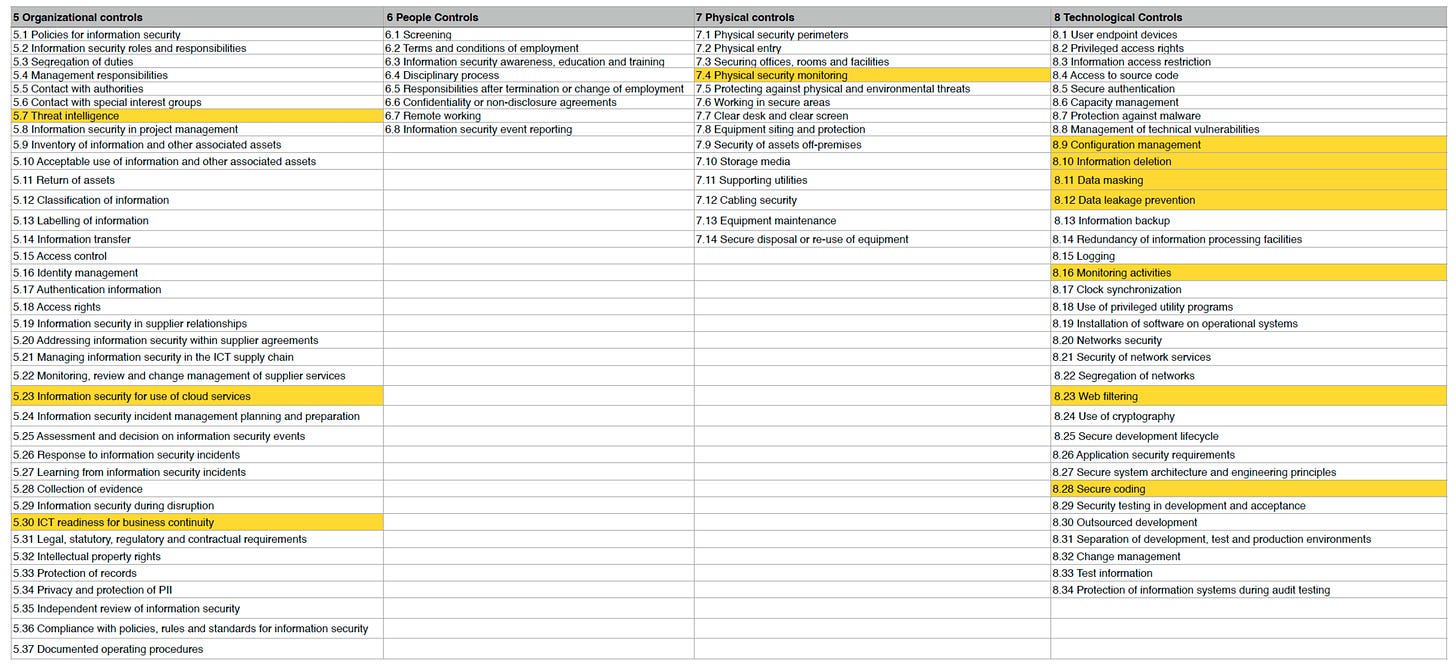
What It Is: Annex A contains 93 information security reference controls across 4 themes, that shall be compared against the controls that have been determined as necessary to treat identified risks.
What It Isn’t: It’s not a detailed control catalogue, describing what must be done.
Let’s look at an example to better understand the difference between the reference controls of Annex A and actual security controls. What about Control A.8.5 Secure Authentication.
A.8.5 Secure Authentication
“Secure authentication technologies and procedures shall be implemented based on information access restrictions and the topic-specific policy on access control.”
As you can tell the example control from Annex A is broad and lacks specifics, such as which technologies to use or how to configure them. It’s merely a description of a desired state but doesn’t go into the specifics. The idea is the following: First, the standard wants you to determine controls that are able to treat your identified risks. Then you must compare them with those listed in Annex A. So, if your organization is facilitating hardware security keys, then obviously those are a form of secure authentication technologies. Therefore control A.8.5 would be necessary, or often expressed as, applicable.
So without actual controls, there is no way to implement A.8.5. What you need are real specific, risk-based controls. Here are practical examples:
Hardware Security Keys: Deploy devices like YubiKey for phishing-resistant authentication, requiring physical interaction for access.
MFA Authenticator Apps: Use apps like Authy for time-based one-time passwords (TOTPs), enforced across all accounts and integrated with identity providers.
Single Sign-On (SSO): Implement SAML-based SSO with providers like Okta, including session timeouts and IP-based restrictions.
Biometric Authentication: Add fingerprint or facial recognition for sensitive systems, paired with liveness detection to prevent spoofing.
Certificate-Based Authentication: Use digital certificates for machine-to-machine access, with automated revocation for expired credentials.
These turn A.8.5 into something tangible, but Annex A doesn’t provide this level of detail. That’s where NIST SP 800-53, or ISO/IEC 27002 comes in.
Why NIST SP 800-53 is a great Companion
NIST SP 800-53 is a comprehensive control catalog with over 1,000 controls across 20 families, designed for federal agencies but adaptable for any organization. Unlike Annex A, it provides actionable, detailed guidance.
Granular Structure: Controls are organized into families like Access Control (AC) and Identification and Authentication (IA), with baselines (low, moderate, high) and enhancements for customization.
Detailed Instructions: For authentication, IA-2 mandates MFA for privileged users, while AC-7 specifies lockout thresholds (e.g., 5 failed attempts in 15 minutes).
ISO Compatibility: NIST controls can map to Annex A, ensuring compliance while strengthening security.
Future-Proofing: Covers modern threats like zero-trust architectures and supply chain risks, with regular updates.
NIST Control Families
Access Control (AC)
Awareness and Training (AT)
Audit and Accountability (AU)
Assessment, Authorization, and Monitoring (CA)
Configuration Management (CM)
Contingency Planning (CP)
Identification and Authentication (IA)
Incident Response (IR)
Maintenance (MA)
Media Protection (MP)
Physical and Environmental Protection (PE)
Planning (PL)
Program Management (PM)
Personnel Security (PS)
PII Processing and Transparency (PT)
Risk Assessment (RA)
System and Services Acquisition (SA)
System and Communications Protection (SC)
System and Information Integrity (SI)
Supply Chain Risk Management (SR)
You can find all controls right here: CSRC
Transitioning to NIST: A Step-by-Step Guide
Here’s how to enhance your ISMS with NIST SP 800-53:
Evaluate Current Controls: Review your Statement of Applicability (SoA) to identify weak Annex A implementations. Use a gap analysis to assess maturity (e.g., is A.8.5 just a policy or fully enforced?).
Map to NIST: Align Annex A objectives with NIST controls using NIST’s mapping tools or a custom spreadsheet. Pair A.8.5 with for example IA-2 (MFA) and IA-5 (authenticator management).
Customize Controls: Select NIST controls based on your risk profile. For example, define standards for hardware keys or integrate SSO with your directory service.
Implement in Phases: Start with pilot deployments (e.g., MFA for admins), then scale enterprise-wide. Update your SoA to reflect NIST enhancements.
Test and Validate: Conduct penetration tests or audits to verify controls. Monitor metrics like failed logins and adjust as needed (e.g., add training from NIST’s AT family).
Maintain and Update: Review annually to incorporate NIST updates, ensuring alignment with new threats.
Key Takeaways
Here is what to remember from this article:
Annex A is a reference for comparison, not a detailed implementation guide.
NIST SP 800-53 provides over 1,000 actionable controls, making it ideal for mature security programs.
Combining NIST SP 800-53 is possible and explicitly allowed by ISO/IEC 27001.
Test your Knowledge
Today’s question is from the CGEIT curriculum:
What is the MAIN benefit of aligning IT performance metrics with business performance metrics?
A) Easier tracking of IT performance
B) Better decision-making for IT investments
C) Increased IT operational efficiency
D) Higher IT team morale
👉 Think you know the answer? Scroll down for the solution!
Answer: The correct answer is B.
A) While tracking may become easier, it's not the main benefit of alignment.
B) Aligning IT metrics with business metrics ensures that IT investments are directly contributing to business goals, facilitating better decision-making.
C) Operational efficiency is important but is a secondary benefit of such alignment.
D) Team morale is important but not the primary reason for aligning IT and business metrics.